Cybersecurity Confidence Starts Here: How 10 Steps Can Strengthen Any Organisation
Cyber threats don’t just target tech giants — they threaten businesses of every size. The NCSC 10 Steps framework offers a proven, strategic approach to strengthen cyber resilience, align boardroom strategy with operational controls, and manage third-party risks. Learn how to assess your cybersecurity maturity, track meaningful metrics, and implement quick wins today. Build confidence, protect assets, and stay ahead of threats before they strike. #CyberSecurity #NCSC10Steps #CyberResilience #RiskManagement
CYBER SECURITY
Toz Ali
6/7/20253 min read


In today’s digital-first world, cyber threats are no longer the domain of tech giants alone. Whether you’re a small startup or a large enterprise, attacks like ransomware, phishing, and data breaches can grind operations to a halt and cost your business dearly. The UK’s National Cyber Security Centre (NCSC) created the 10 Steps to Cyber Security as a powerful framework to help any organisation proactively build cyber resilience.
This in-depth guide explores what the 10 Steps are, why they matter, how they benefit businesses of all sizes, how they compare with other frameworks, how to implement them effectively, and how to use them to assess cybersecurity maturity and track meaningful performance metrics. While it may take up to 10 minutes to read, this resource is designed to give you a practical understanding of how to embed cybersecurity resilience across your organisation.
What are the NCSC 10 Steps to Cyber Security?
The NCSC 10 Steps is a strategic framework comprising ten key areas of cybersecurity best practice:
Risk Management – Understand and manage risks to systems, data, and services.
Engagement and Training – Educate and empower staff at every level.
Asset Management – Know what technology and data you hold and where they are.
Architecture and Configuration – Build systems securely from the ground up.
Vulnerability Management – Identify and patch known weaknesses.
Identity and Access Management – Ensure only the right people access the right systems.
Data Security – Protect information in storage and transit.
Logging and Monitoring – Track activity to spot and investigate incidents.
Incident Management – Prepare for and respond to cyber incidents effectively.
Supply Chain Security – Assess and manage risks from third-party providers.
It’s a coordinated, comprehensive approach to securing people, processes, and technology.
How It Will Benefit Small, Medium, and Large Organisations
Small Businesses
Stop common attacks with strong passwords, regular updates, and backups.
Win new contracts by proving security to larger clients.
Improve cost-effectively using NCSC's free guidance and tools.
Medium-Sized Organisations
Reduce exposure to ransomware and data loss.
Create a security culture through structured training and awareness.
Improve compliance and risk governance.
Large Enterprises
Unite boardroom strategy with operational execution.
Scale security controls consistently across teams and locations.
Raise assurance standards for third-party providers.
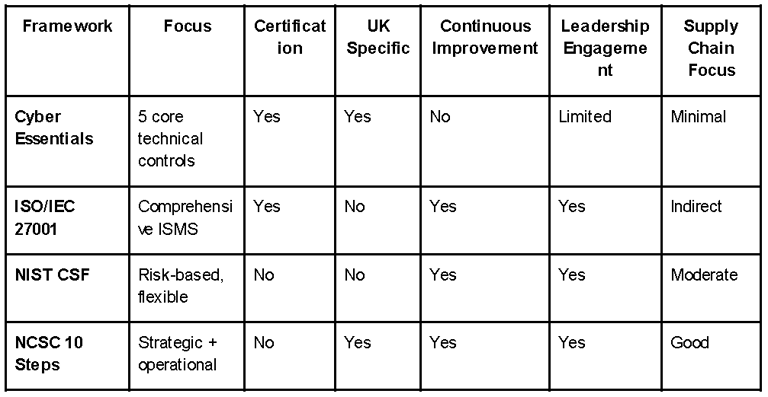
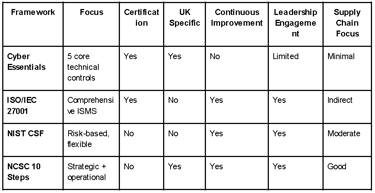
Comparison with Other Frameworks
Why the 10 Steps Stand Out: Key Differentiators
Strategic and Practical – Combines board-level guidance with day-to-day actions.
Boardroom to Server Room – Makes cybersecurity everyone's responsibility.
No-Certification Barrier – Enables rapid uptake without bureaucracy.
Tailored to UK Risk Landscape – Reflects domestic threats and legal context.
Scalable and Adaptable – Suitable for any size, sector, or maturity level.
Strong Supply Chain Focus – Provides dedicated structure for third-party risk.
How to Implement the 10 Steps in an Organisation
Conduct a Gap Analysis – Highlight control gaps and prioritise based on risk.
Create a Cybersecurity Roadmap – Break work into achievable, phased milestones.
Gain Leadership Support – Align cybersecurity with business goals.
Quick Wins – Deploy MFA, secure backups, and run phishing awareness training.
Invest in Tools and Partners – Use NCSC tools (e.g., Logging Made Easy) and commercial platforms.
Evolve and Improve – Continuously reassess and update controls and strategy.
Using the 10 Steps to Assess Cyber Maturity and Collect Metrics
Assessing Organisational Maturity
Each step can be rated on a scale (e.g. 1–5) to:
Establish a security baseline
Highlight specific weaknesses
Plan maturity goals and improvements
Example of controls:
Risk Management – Do you have an active risk register? Is it regularly reviewed?
Access Management – Is MFA enforced for all users? Are dormant accounts removed?
Collecting Cybersecurity Metrics
The NCSC 10 Steps framework provides a structure that organisations can use to define, collect, and analyse cybersecurity metrics. Each step represents a domain of security that can be measured using meaningful indicators:
Risk Management – Number of identified risks, treatment rate, review frequency
Engagement and Training – % staff trained, phishing test success rate
Asset Management – % of inventoried assets, frequency of updates
Architecture and Configuration – % of systems with secure configurations
Vulnerability Management – Patch latency, scan coverage
Identity and Access Management – % of MFA use, number of dormant accounts
Data Security – % of encrypted data, DLP events
Logging and Monitoring – % of systems monitored, alert response time
Incident Management – Mean time to detect and recover, exercise frequency
Supply Chain Security – % of suppliers assessed, % with contract clauses
These metrics support:
Board-level reporting
Cyber investment planning
Strategic risk governance
Downloadable Template of the Controls (Coming Soon)
Download the NCSC 10 Steps Maturity Assessment Template:
Benchmark your cybersecurity maturity
Assign responsibilities and actions
Track progress across all 10 Steps
Final Thoughts
The NCSC 10 Steps to Cyber Security is more than a framework—it's a roadmap for embedding security into the DNA of your organisation. It helps you move from reactive to proactive, from fragmented efforts to a unified strategy.
Whether you’re managing a team of 10 or 10,000, the 10 Steps offer scalable guidance backed by UK government expertise. Use them to build confidence with stakeholders, improve compliance, and stay ahead of evolving threats.